Introduction
Despite Yemen’s ongoing civil war, which saw the Iran-backed Houthis seize power in 2014, the country’s telecommunications industry has continued to grow. According to a recent U.N. report, since 2014, the number of mobile phone subscriptions has increased by nearly 20 percent to 18.6 million, while the number of Internet users has more than doubled to 7.2 million.* The figures should indicate that the Yemeni people have greater access to information and could, in turn, provide the outside world additional information about Yemen. However, with the Houthis’ powerful control of the telecommunications industry in Yemen, the population’s growing connectivity is a double-edged sword.
This report will shed light on the Houthis’ use of Yemeni telecommunications infrastructure to control the information environment. In particular, it will focus on the mobile network operators (MNOs) and Internet Service Providers (ISPs) in Yemen. Regarding the MNOs, it will discuss how the Houthis exert control over key companies in this space, what type of intelligence their control provides them, and activities the group undertakes to supplement this intelligence. As for the Internet, the report will identify how the Houthis control this infrastructure and use it for censorship.
The research will also identify which officials, companies, and individuals play leading roles in building up the Houthis’ technological capabilities for censorship and surveillance. Notably, there are U.S. government precedents* for sanctioning entities involved in such activities in other countries, including:
- Executive Order (E.O.) 13846, which authorizes sanctions for censorship or other activities with respect to Iran; and
- E.O. 13606, which authorizes sanctions for grave human rights abuses by the governments of Iran and Syria via information technology.
The Houthis and MNOs: A Valuable Source of Revenue and Intelligence
Background on Yemen’s MNOs
In 2001, the first tenders were issued to MNOs in Yemen, and since then, the market has expanded to around 70 mobile subscriptions for every 100 people.* The Yemeni MNO landscape includes three significant players that comprise more than 90 percent of the market: Yemen Mobile (40 percent), Sabafon (28 percent), and MTN Yemen/Yemen Oman United (YOU) telecom (27 percent).* Since the outbreak of the Yemeni civil war in 2014, the Government of Yemen (GOY) and Houthis have been in a struggle to gain control of the cellular providers and their infrastructure.




The Houthis, due to their control of the Ministry of Telecommunication and Information Technology (MTIT) in Sanaa, have a controlling stake of Yemen Mobile. While Yemen Mobile was previously viewed as the only MNO that serves both Houthi-controlled and government-controlled territory, the GOY has recently banned the repair or modernization of Yemen Mobile infrastructure in its territory.*
Sabafon was initially based in Sanaa but several years after the 2014 Houthi takeover, the company’s ownership decided to move the organization to Aden. According to Sana’a Center for Strategic Studies, the 2020 move to Aden “was to avoid paying the fine,* to disengage its network from Houthi wiretapping of customers, and to prepare for expansion into fourth and fifth generation mobile phone services.” But rather than leaving the capital city entirely, the company appears to have split into Sanaa-based* and Aden-based entities* bearing the same name. Due to Houthi directives following Sabafon-Aden’s departure, the Sabafon-Aden’s subscribers can no longer call Sabafon-Sanaa subscribers (or subscribers of any other Houthi-controlled MNOs). Since the split, Houthi missile strikes have targeted and severely damaged Sabafon-Aden’s cellular infrastructure.*
MTN Yemen was based in Sanaa until 2021, when the South African conglomerate “sold” its shares of the company, reportedly to an Omani conglomerate, despite the GOY’s opposition to the deal. The acquired company resumed operations from Sanaa under the new brand
The takeover of MTN Yemen in 2021 is an intriguing example in the struggle to control Yemen’s MNOs. The following section is a product of intensive research, and the information uncovered raises many red flags regarding potential corruption in the “gifting” of a company with tens if not hundreds of millions of dollars in annual revenues.
Exchanged for a Quarter: The Curious Acquisition of MTN Yemen
In principle, MTN’s departure from Yemen in November 2021 should not have come as a surprise as this was supposedly* part of the company’s declared strategy to disengage from the Middle East and focus on African markets. Around the same that it withdrew from Yemen, the South African telecom giant also departed from both Syria and Afghanistan. MTN’s desire to leave Yemen was probably related to several intertwined issues, which created a challenging business environment in Yemen, particularly:
- Telecommunications is one of the largest sectors of the Yemeni economy in terms of revenue generation. As such, telecommunications companies are prime targets for extortion attempts by Yemeni powerbrokers, a practice made possible by Yemen’s corrupt and dysfunctional business/regulatory environment;
- The Houthis’ totalitarian rule in Sanaa presented an ongoing risk of expropriation;*
- The risks and complications of maintaining telecommunications infrastructure during an ongoing civil war; and
- A destitute population which translates into fairly limited market potential.
What is truly interesting is not that MTN withdrew from Yemen, but how they did so.
One United Arab Emirates dirham (about 25 cents in U.S. currency) is all that MTN was paid for a controlling share in the company, which held about 30 percent of the MNO market in Yemen.* This seems like an unusually small payment for a large stake of a market valued at hundreds of millions of dollars. The sequence of events in Yemen was also unique when compared with MTN’s withdrawals from Afghanistan and Syria. In Afghanistan, the company received $31 million dollars in exchange for its shares of MTN Afghanistan, and in Syria, where MTN was forced out by the “Syrian court system,” the company declared its right to seek redress in international court.* In Sanaa, when MTN pulled out, it appears to have neither been sufficiently compensated nor did it claim that it should.
No less surprising is the new owner of MTN Yemen: a company named Emerald International Investment (EII), a holding company which was registered about two weeks before it gained a controlling stake in MTN Yemen.* According to MTN, “Emerald is a subsidiary of Zubair Investment Center LLC, an affiliate of Zubair Corporation LLC, which is the minority shareholder in MTN Yemen.”* The narrative was that EII’s takeover of MTN Yemen was essentially a minority owner of the company gaining majority control. But the actual shareholders of EII are Oman-based holding company Arkan International Modern Investment (AIMI) (99 percent) and a Yemeni national by the name Marwan Mohammed Khaled Mohammed (one percent).*
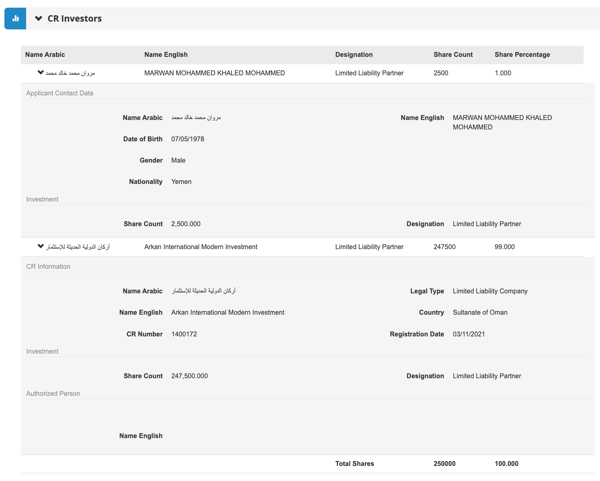
Little is known about the mysterious shareholders of EII who acquired MTN Yemen.
Little if any information, beyond a bare-bones website for “Arkan Investments” in Oman potentially linked to AIMI,* is available about the new owners of one of Yemen’s largest MNOs.* Based on the registered shareholders, there is no indication that EII is owned by Zubair. In fact, the only EII-Zubair connection is the contact email listed in EII’s registration: [email protected]. Qais Al Batashi was appointed Zubair’s Head of Public Relations, though it was acknowledged that he was fairly young for such a role,* and then approximately six weeks later he became the point of contact for this telecom acquisition.
AIMI, the owner of 99 percent of EII, is not owned by Zubair* and was registered as a corporation in Oman one day after EII.* It appears to be owned by two Yemeni nationals, one of whom is a partial owner of EII alongside AIMI: Marwan Mohammed Khaled Mohammed and the other is Abdullah Mohammed Abdullah Al Naggar. The contact details for AIMI are a Yahoo email address ([email protected]) and a telephone number (96960445) which appears fraudulent. In contrast to the contact phone number listed for EII, this telephone number does not comply with any known country code or regional telephone format. Further, the company address on its registration does not list a specific street.*
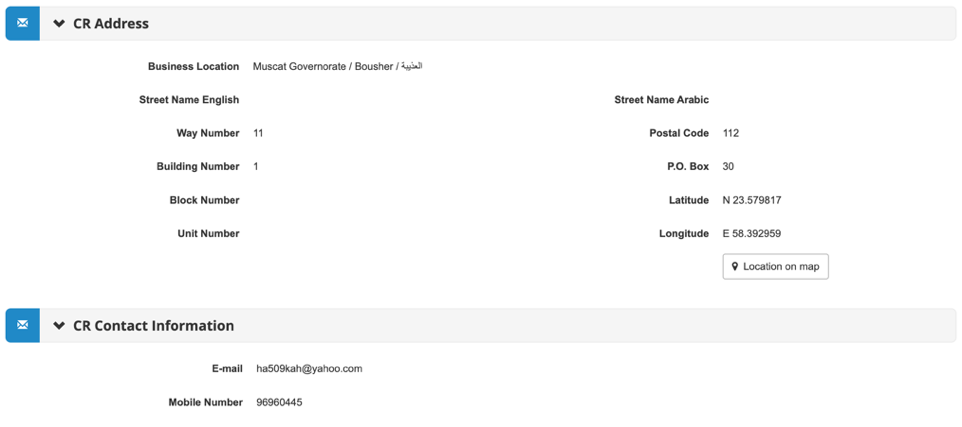
AIMI was the major shareholder of the company that acquired MTN Yemen. It provided little contact information in its business registration in Oman, and whatever details it did provide appear dubious.
Any theories about who was behind EII’s acquisition of MTN Yemen and its transformation into YOU telecom would be speculation. However, given the importance of the telecommunication industry in Yemen, the GOY’s opposition to the 2021 transaction* and the Houthi’s complete silence on the matter is telling. In addition, it is notable that MTN has since been enabled to operate from Houthi-controlled Sanaa under the new YOU telecom brand and was swiftly banned by the GOY.
Houthi Surveillance and Spyware
Houthi surveillance measures are directed at their opponents within Yemen—both in territories under their direct control and outside of it. As early as 2015, a news report from a Yemeni website quoted an anonymous Yemen Mobile employee saying, “Houthi group and Saleh loyalists monitor all communications and text messages of phones located on battlefields throughout the country… a special team trained by the Houthis carries out this task day and night.”* By exploiting tools designed for law enforcement purposes, the Houthis are able to yield information on the private communications of the mobile subscribers of the Sanaa-based MNOs.
Collection of cellular communications is hardly a new or particularly complex challenge for governments working in cooperation with cellular providers. Lawful interception is a basic function that all governments are able to conduct in order to view incoming and outgoing communications (i.e., calls and text messages) for particular mobile subscribers. In the Houthis context, however, this likely serves as a source for intelligence on enemy planning, counterintelligence on domestic opponents of their regime, and kompromat to blackmail Sanaa’s enemies. Therefore, it should come as no surprise that that the Houthis are doing their utmost to maintain this resource by holding on to their “monopolistic market share throughout the whole country…[to]not allow the growth of rival telecommunications companies based in Aden.”*
There are numerous allegations regarding the extent and capabilities of the Houthi wiretapping. One article associated with Yemen’s al-Islah Party noted, “the new Houthi leadership that runs the Yemen Mobile Company has placed more than 3,000 military and civilian personnel of the GOY under surveillance and wiretapping.”* Regarding Houthi capabilities, it explained that the group is able to monitor communications based not only on the SIM card but also on the unique identifier for the device itself (presumably the IMEI) to ensure that even individuals under surveillance who switch SIMs as a countersurveillance measure cannot evade Houthi tracking.* Several sources also allege that Iran and Iranian-sponsored terrorist group Hezbollah play significant roles in supervising the Houthi mobile surveillance apparatus and providing it with advanced surveillance equipment. *
Yet, classic lawful interception does not provide a solution for on-device data that has not transited the mobile network, nor does it cover encrypted Internet-based communications (e.g., WhatsApp, Signal, etc.). Therefore, it is worth noting that official government statements* as well as leaked emails* indicate GOY forces in Sanaa sought to acquire more intrusive capabilities to hack mobile devices (commonly known as “spyware”) prior to the 2014 Houthi takeover. Whether European spyware vendors sold to the GOY remains unknown, as Citizen Lab was unable to find any evidence indicating that they had.* Nonetheless, capabilities purchased in 2014 would be outdated to the point of irrelevance.
Interestingly, in May 2023, Recorded Future published a report entitled “OilAlpha: A Likely Pro-Houthi Group Targeting Entities Across the Arabian Peninsula,” which shed new light on spyware use against the Houthis’ enemies.* Hackers reportedly utilized remote access trojans (RATs) to target Android-based devices belonging to individuals working as political representatives, journalists, and NGO workers affiliated with the GOY, Saudi Arabia, or the UAE. The hackers used sophisticated social engineering tactics via end-to-end encrypted instant messaging applications like WhatsApp to deliver malicious links to the targets. Once the target fell for the ruse and unknowingly provided access to his device, the group was enabled to access far more information than would be available from a simple wiretap, including “call logs, SMS data, contact information, network information… the device’s camera and audio, as well as GPS location data, among others.”*
The conclusion that these attacks were (and continue to be) launched at the behest of the Houthis is based on the fact that infrastructure used for the command and control belongs to the Houthi-controlled Public Telecommunication Corporation (PTC). The report also assessed that the Houthis are the singular organization with motive to surveil those who fit the profile of the targets. However, it is possible that the Houthis are not directly engaged in these efforts, and they may have contracted this activity out to “external threat actors like Lebanese or Iraqi Hezbollah, or even Iranian operators supporting the IRGC [Islamic Revolutionary Guard Corps].”*
Internet in Yemen: Houthis Control and Exploitation
Background
Internet was first made available to Yemenis in 1996 by TeleYemen, a joint U.K.-Yemeni venture that served as the country’s first Internet Service Provider (ISP). In 2001, the GOY created an alternative ISP called YemenNet, which has since become the practically unrivalled provider to the Yemeni market. Then, in 2004, TeleYemen also came under full GOY control, and it continues to maintain control of the country’s significant Internet Gateways (i.e., pathways for Internet traffic in and out of Yemen). As both major players in Yemen’s Internet infrastructure were government-owned by 2004, the industry was centralized and fairly easy to regulate.
Since the Internet’s advent to Yemen, contents were filtered by the government of Ali Abdullah Saleh.* After Saleh’s fall in 2012 and the Houthi takeover of Sanaa in 2014, Internet censorship intensified. With the 60-70 percent of the Yemeni population living under their rule, the Houthis’ control of the country’s ISP granted them the ability to control what information the majority of Yemenis could access.
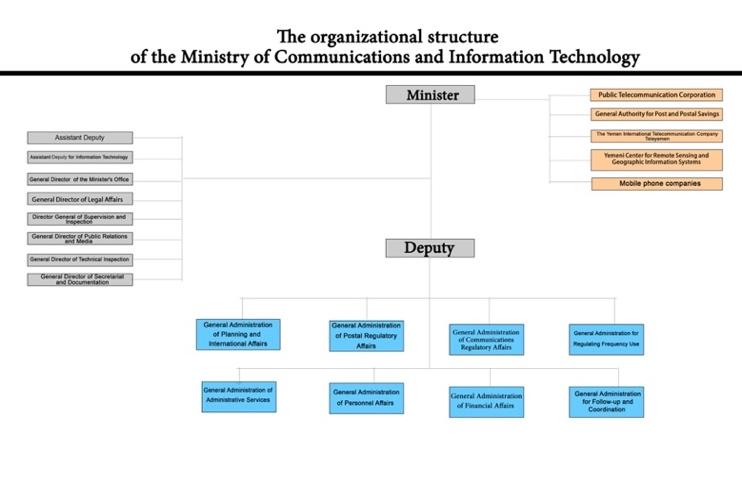
While this chart is from thewWebsite of the MTIT of the GOY, it more accurately reflects the MTIT of the Houthis. According to the U.N., "The ministry of telecommunications and information technology responsible for the areas under the control of the Houthis is the overarching body that performs all types of roles concerning this sector."*
Prior to 2014, TeleYemen and YemenNet operated under the auspices of the MTIT. TeleYemen reported directly to the minister, while YemenNet operated under the authority of the MTIT’s PTC. After the Houthis stormed Sanaa, they appear to have maintained that same structure. However, the minister in charge was no longer from the GOY, but rather an appointee of the Houthis Supreme Revolutionary Council. Those appointed by the Houthis as minister in charge of overseeing the MTIT and TeleYemen include: Musleh Mohsen Al-Uzair, then Jlidan Mahmoud Jlidan, and since December 2017, the role has been filled by Misfer al-Numeir. PTC, charged with managing YemenNet, is administered by Director General Sadiq Muhammad Musleh and his deputy Taha Muhammad Zabara.



Houthi Ministers of MTIT: Former Deputy/Acting Minister Musleh Mohsen Al-Uzair, 2015-2016 (left);* Jlidan Mahmoud Jlidan, 2016-17 (center);* and Misfer al-Numeir, 2017-Present (right).*


PTC Director General Sadiq Muhammad Musleh (left)* and his deputy Taha Muhammad Zabara (right).
Internet Censorship and Surveillance
Since taking control of Yemen’s Internet, the Houthis sought to influence Yemeni society to accept their radical regime by saturating the information space with media supporting their narrative and blocking out websites and platforms that did not comport. Their approach appears to have worked. In 2021, around 80 percent of people living under Houthi rule trust their local officials to provide accurate information, while only about a quarter of those living in government-controlled territories said the same of those in-charge.* One might argue that the Houthis have earned the trust of the people through a variety of methods including good governance, but there does not appear to be much evidence to support such an explanation. * The creation of a hermetically-sealed and Houthi-controlled information bubble better explains the phenomenon, and it fits neatly with what Michael Knights describes as instances where Houthi troops are captured and then shocked to find out that all along they were fighting against fellow Yemenis rather than Americans or Israelis.*
It is noteworthy that the Houthis have taken legal measures to ensure that narratives or news contrary to their own would not be published on the Internet. For example, in 2017, the Houthis banned operating news websites without formal approval and reserved the right to ban any sites publishing information that they found objectionable.* However, this step only serves to control what is posted from within Yemen and does not impact what external entities can post on the Internet for Yemenis to see.
While the Houthis may have been dismissed as “unsophisticated” before, during, and after they stormed Sanaa in 2014, their quick moves to exert tighter control on the information accessible to Yemenis indicates otherwise. According to Citizen Lab, by 2015, the group had used YemenNet’s existing infrastructure and capabilities to filter out content and limit the information available to Yemenis with Internet access.* The NGO’s 2015 report concluded that the following types of content were newly blocked:
- Sites with a URL that included Israel’s top-level domain (URLs that end with “.il”);
- Domestic independent news outlets reporting negatively on the Houthis or their allies;
- Websites of local political parties opposed to the Houthis;
- Foreign mainstream Arabic news outlets, like Al Arabiya and Al Jazeera; and
- Websites that promote secular/Christian/un-Islamic doctrines.
When trying to access specific websites via YemenNet, it was evident from the error messages that appeared on-screen which company had provided the Internet filtering technology. NetSweeper, a Canadian company which has provided similar solutions for a number of Gulf governments,* enabled its product for YemenNet well before the Houthis stormed Sanaa. Following the Houthi takeover, the definition of permissible content allowed to pass through the filter narrowed significantly.
NetSweeper initially threatened to sue Citizen Lab for defamation following the publication of its 2015 report.* However, the company dropped the suit by 2016. In advance of the publication of the 2018 report documenting the continued use of NetSweeper capabilities by YemenNet, the Canada-based company responded to the findings by noting its compliance with Canadian law and dilemmas facing “every major developer of IT solutions.”*
At the time of this writing, it is not known whether NetSweeper’s technology remains in use by the Houthis. However, a 2019 Recorded Future report noted “an increase in the deployment of network control devices on YemenNet, the ISP controlled by Houthi forces.”* The report also mentioned also mentioned YemenNet’s “deployment of two additional NetSweeper devices” and “purchase of a large amount of equipment from Chinese telecommunications company Huawei.”
Since 2015, Houthi Internet censorship has likely expanded from simply filtering out websites to active monitoring of Internet activity. A 2022 report by the U.N. Panel of Experts on Yemen noted that Houthi-controlled TeleYemen* purchased a “bandwidth management system” for Deep Packet Inspection (DPI). The deployment status of this capability is not explicitly stated in the report, but the “bandwidth management system” appears to be in use based on TeleYemen’s unconvincing denial that it is being misused.* The Houthi’s longtime control of Yemen’s top-level domain (URLs that end with “.ye”) combined with DPI provides the group with almost absolute control of the Internet in Yemen. As noted in the U.N. report, the Houthis now have the “capacity to monitor and interdict traffic, censor content, carry out Internet shutdowns, ban social media sites and personal messaging services, monitor private communications of opponents and block domains in all parts of the country.”* The 2023 U.N. Panel of Experts report on Yemen notes that Houthis efforts to smuggle unauthorized telecommunications equipment into Yemen are ongoing and intensive, if not always successful.*
Analysts have suggested that the Houthis seek to strike a delicate balance between limiting their population’s access to information and enjoying tens of millions of dollars in potential revenues that they can reap from their control of the countries two main ISPs.* They have increased prices (dollar per gigabyte, $/GB) to the point where surfing the web on a mobile device in Yemen is more than twice the price of doing so in the second most expensive country to do so in the Middle East: $16/GB in Yemen compared to around $6/GB in Syria.* This is prohibitively expensive for many in Yemen, where the GDP per capita is around $700.* In addition, the Houthi failure to invest in maintaining, repairing, and upgrading infrastructure has made Internet in Yemen not only expensive, but also extremely slow—if not the slowest in the world.*
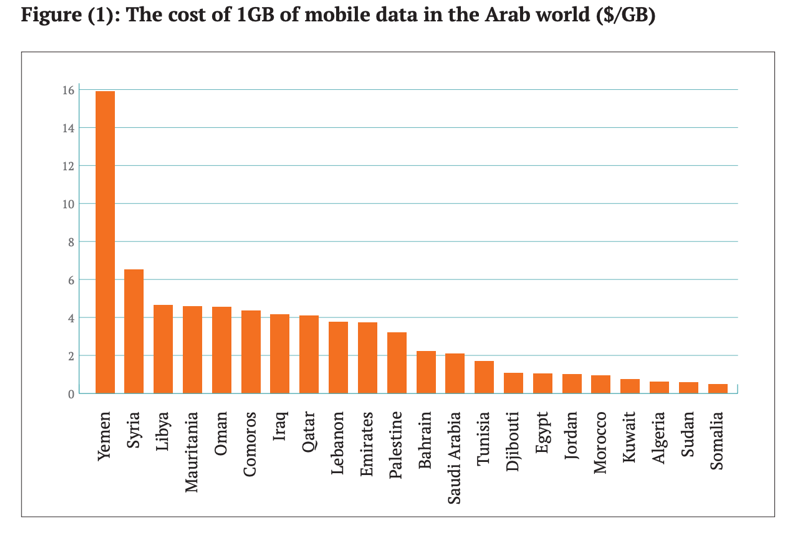
Yemeni Internet prices ($/GB) for using the Internet on mobile devices are more than ten times the price in Egypt or Jordan.*
While Virtual Private Networks (VPNs) do offer solutions that protect privacy through encryption and enable workarounds to content restrictions, they are not a panacea for Yemenis in search of secure access to content blocked in Yemen. Most attempts to access VPNs are blocked by Yemeni Internet controls,* the vast majority of the Yemeni population is not technologically literate enough to know about this possible solution or how to use it,* and using VPNs makes an already expensive and slow Internet experience even more so.*
To avoid providing income and intelligence to the Houthis and to evade the group’s integrated censorship,* the GOY has sought to provide alternatives to the Houthi-controlled ISPs. With that in mind, it founded AdenNet in 2018. However, this effort has been slow to yield results. Five years later, the company is only able to provide limited Internet coverage to specific areas of Aden.
Conclusion
The root of the censorship and surveillance problem is Houthi control of the telecom providers (ISPs and MNOs), which become accomplices to the movement’s totalitarian rule. Individuals and entities engaged in the worst practices of corruption and violations of basic human rights, including relevant officials from the MTIT, PTC, YemenNet, TeleYemen, and the YOU telecom acquisition scheme, ought to be sanctioned. The U.S. sanctions framework for doing so is either Global Magnitsky Act (formally known as the Russia and Moldova Jackson–Vanik Repeal and Sergei Magnitsky Rule of Law Accountability Act of 2012) or a new E.O. analogous to E.O. 13846 or E.O. 13606, which target entities involved in technological repression elsewhere in the Middle East.


TeleYemen CEO Ali Nagi Nosari(left)* and Director General of YemenNet Taha Ahmed al-Rada’i.*
Steps against Yemeni telecommunications companies and their co-conspirators should be surgical. Drastic steps like immediately cutting off TeleYemen’s connection to the Internet would certainly punish those companies, but it would also be a golden opportunity for the Houthis as it would make them an uncontested source of “information.”
The aim should be to weaken and punish the offending entities while enhancing the position of the Yemeni people. The accomplices of Houthi corruption and human rights violations should be isolated, denied access to the U.S. financial system, prevented from building international partnerships, and blocked from acquiring state-of-the-art equipment that could enhance their commercial offerings or be used for surveillance purposes. But such steps will only yield significant results if connected to a comprehensive strategy, which aims to create better and safer alternatives to these companies.
 TOP
TOP